0x00Sec CTF 1st Challenge
Was browsing reddit this morning and saw the 0x00Sec post about a CTF, so I figured I’d give it a shot. The first CTF challenge was pretty easy and it started with a login page prompt.
First step, inspect the page – Found some interesting comments.
Poked a couple urls
- https://exercise-1.0x00sec.dev/.git/ (permission denied)
- https://exercise-1.0x00sec.dev/.git/config
Then with some helpful googling, I found this resource. Great content as always from pentester.land, which led me to the tool GitTools. Fired that bad boy up and dumped and extract the git content which lead to the source:
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no">
<meta name="description" content="">
<meta name="author" content="">
<title>Hack this :)</title>
<link rel="canonical" href="https://getbootstrap.com/docs/4.0/examples/sign-in/">
<!-- Bootstrap core CSS -->
<link href="https://stackpath.bootstrapcdn.com/bootstrap/4.3.1/css/bootstrap.min.css" rel="stylesheet">
<!-- Custom styles for this template -->
<link href="https://getbootstrap.com/docs/4.0/examples/sign-in/signin.css" rel="stylesheet">
</head>
<body class="text-center">
<?php
function xor_this($string, $supplied_key) {
// Let's define our key here
$key = ($supplied_key);
// Our plaintext/ciphertext
$text = $string;
// Our output text
$outText = '';
// Iterate through each character
for($i=0; $i<strlen($text); )
{
for($j=0; ($j<strlen($key) && $i<strlen($text)); $j++,$i++)
{
$outText .= $text{$i} ^ $key{$j};
}
}
return $outText;
}
if (isset($_POST["username"]) && isset($_POST["password"])) {
if ($_POST["username"] == "admin" && hash('sha256', $_POST["password"]) == "e83176eaefcc1ae8c4a23dbc73ebcf122f26cfb9ba5c7cf4763e96c1c38a6c6c") {
echo '<h4> '.xor_this(base64_decode("Cl9SEwgSQRVFUA1dAl1dVFkaQF0CWAQUTQ=="), $_POST["password"]).' </h4>';
} else {
echo '<h4 class="error"> Incorrect Password :) </h4>';
}
} else {
echo '
<form class="form-signin" action="/" method="post">
<h3> 0x00sec Exercise #1 </h3>
<label for="inputEmail" class="sr-only">Username</label>
<input type="text" id="inputEmail" name="username" class="form-control" placeholder="Username" required autofocus>
<label for="inputPassword" class="sr-only">Password</label>
<input type="password" id="inputPassword" name="password" class="form-control" placeholder="Password" required>
<button class="btn btn-lg btn-primary btn-block" type="submit">Login</button>
</form>';
}
?>
</body>
<!-- TODO: -->
<!-- * Remove the git directory after publishing -->
</html>
One thing stuck out to me in the source immediately:
if ($_POST["username"] == "admin" && hash('sha256', $_POST["password"]) == "e83176eaefcc1ae8c4a23dbc73ebcf122f26cfb9ba5c7cf4763e96c1c38a6c6c")
if username is admin && the hash256 password param is equal to that hash e83176eaefcc1ae8c4a23dbc73ebcf122f26cfb9ba5c7cf4763e96c1c38a6c6c then it will show you the flag. So I went ahead and looked up a rainbow table and plugged the hash in.
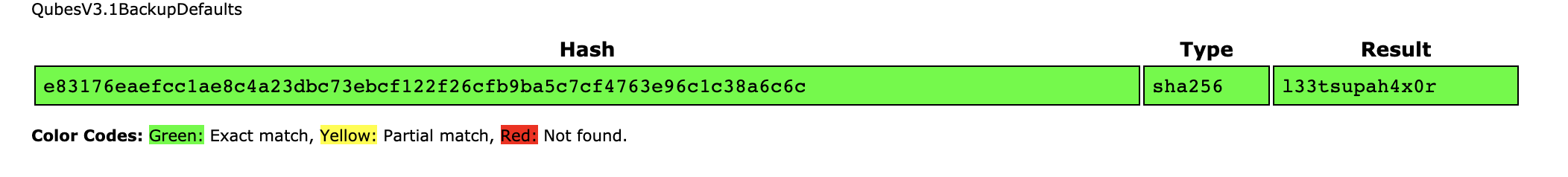
Turns out the password was l33tsupah4x0r and thus gives you the flag!
Thanks for reading…see you next time.